
Complete Cyber Security and Visibility for ICS Environments

Immediately
Visualize and Explore
Industrial Networks

Quickly Identify
and Address
Vulnerabilities

Automatically Track
Industrial Assets and Know
Their Cyber Security Risks

Rapidly Detect Cyber
Threats/Risks and
Process Anomalies

Continuously
Monitor ICS Risks
and Processes
Easily Integrate
with SOC/IT Tools
and Workflows
Guardian™ protects your control networks from cyberattacks and operational disruptions by providing complete ICS visibility and security in a single, unified solution.
Its advanced technology automatically maps and visualizes your entire industrial network, including assets, connections, and protocols. Guardian monitors network communications and behavior for risks that threaten the reliability of your systems, and provides the information you need to respond quickly.
Available as a passive monitoring solution, or a low-impact active solution with the Smart Polling™ add-on, Guardian allows you to choose the asset discovery approach that best fits your organization.
Guardian delivers:
- Superior asset identification, network visualization and ICS risk monitoring
- Real-time ICS threat, anomaly and vulnerability detection
- Enterprise-class scalability when deployed with the Central Management Console™ (CMC)
- Seamless integration with other security and IT tools
Find out how customers improve the reliability, cyber security and operational efficiency of their facilities with Guardian.
Superior Operational Visibility
- Intuitive network visualization
- Automated asset inventory
- Real-time network monitoring
The Best ICS Threat Detection
- Behavior-based anomaly detection
- Rules and signature-based threat detection
- Advanced correlation for detailed insights and rapid remediation
- OT ThreatFeed™ subscription ensures rapid detection of emerging risks
Extensive Global Installations
- Multinational deployments with hundreds of facilities and thousands of devices
- Monitors and reduces OT risks in sectors such as critical infrastructure, energy, manufacturing, mining, transportation and utilities
Time-Saving Forensic Tools
- Dynamic Learning™ that reduces false alerts
- Automatic packet capture
- TimeMachine™ system snapshots
- Real-time ad hoc query tool
Superior ICS Network and Operational Visibility
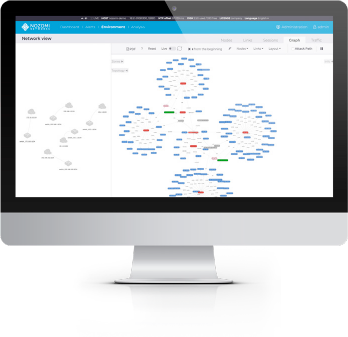
Immediately Visualize Your Industrial Network
Real-time Network Visualization
- Improves system awareness and understanding of network structure and activity
- Displays key information such as traffic throughput, TCP connections, and the protocols used between nodes and zones
- Speeds incident response and troubleshooting efforts
Flexible Navigation and Filtering
- Shows macro views plus detailed information on endpoints and connections
- Filters by subnets, network segments and topologies
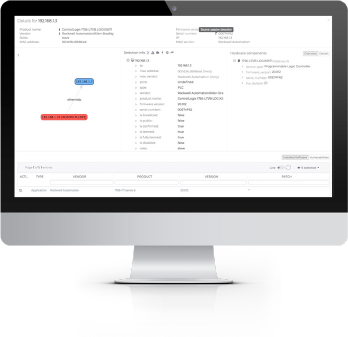
Automatically Track Your Industrial Assets
Up-to-Date Asset Inventory
- Advances cyber resiliency and saves time with automated asset inventory
- Provides detailed and verified asset information
- Identifies communicating assets using built-in passive network monitoring
Enhance Asset Tracking with Smart Polling Add-on Module
- Discovers silent and rogue assets with active discovery
- Includes firmware versions, patch levels and more
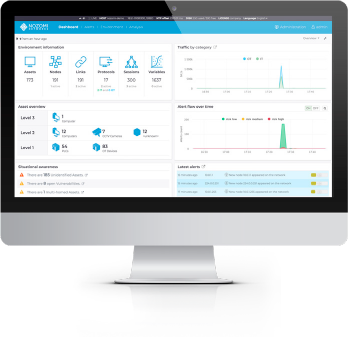
Continuously Monitor Your Network and ICS
Comprehensive Cyber Security and Reliability Monitoring
- Improves network security and productivity through dashboards, charts and queries relevant to your organization
- Monitors assets from all vendors and all network communications
Clear Presentation of Key Metrics
- Displays summarized data related to alerts, incidents, vulnerabilities, etc.
- Includes indicators of reliability issues such as unusual process values
Easy Access to ICS Data
- Summarizes ICS risk information for selected date and time ranges
- Supports drilldown on visual indicators for detailed information
- Queries any aspect of your network or ICS
The Best ICS Threat Detection
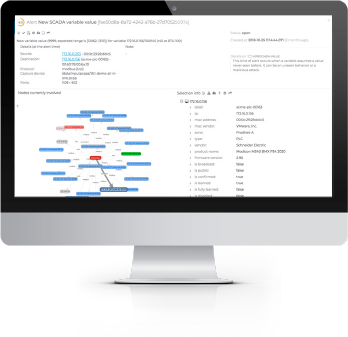
Quickly Detect Threats to Your ICS or SCADA System
Up-to-the-Minute Threat Detection
- Identifies cyber security and process reliability threats in real-time
- Detects attacks in process, early stage advanced threats and cyber risks
- Blocks attacks when integrated with compatible firewalls
Best-in-Class ICS Threat Detection
- Uses anomaly and signature-based threat detection for comprehensive risk detection
- Ensures current monitoring when integrated with OT ThreatFeed subscription
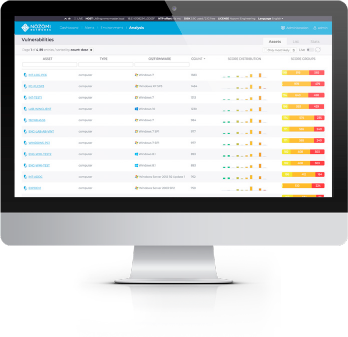
Rapidly Identify Your Vulnerability Risks
Automated Vulnerability Assessment
- Identifies which vendors’ devices are vulnerable
- Utilizes the U.S. government’s National Vulnerability Database (NVD) for standardized naming, description and scoring
Efficient Prioritization and Remediation
- Speeds workflows with vulnerability dashboards and drilldowns
- Addresses questions like “Do certain devices have vulnerable firmware?”

Reduce Troubleshooting and Forensic Efforts
Effective, Efficient Incident Response
- Minimizes false positives with AI-powered Dynamic Learning
- Decreases response time with Smart Incident™, which correlates alerts, provides operational context and delivers automatic packet captures
Informative Forensics
- Decodes incidents with Time Machine™ system snapshots and diff reports (Snapshots are dynamic, allowing drilldown into rich ICS data.)
- Provides answers fast with a powerful ad hoc query tool
